Illuminate Your Game: Billiard Table Lighting Tips
Discover the best lighting solutions for your billiard table to enhance your game and ambiance.
RFID: The Secret Life of Your Everyday Objects
Unlock the hidden world of RFID technology and discover how it connects your everyday objects! Dive in and be amazed!
How RFID Technology is Revolutionizing Everyday Items
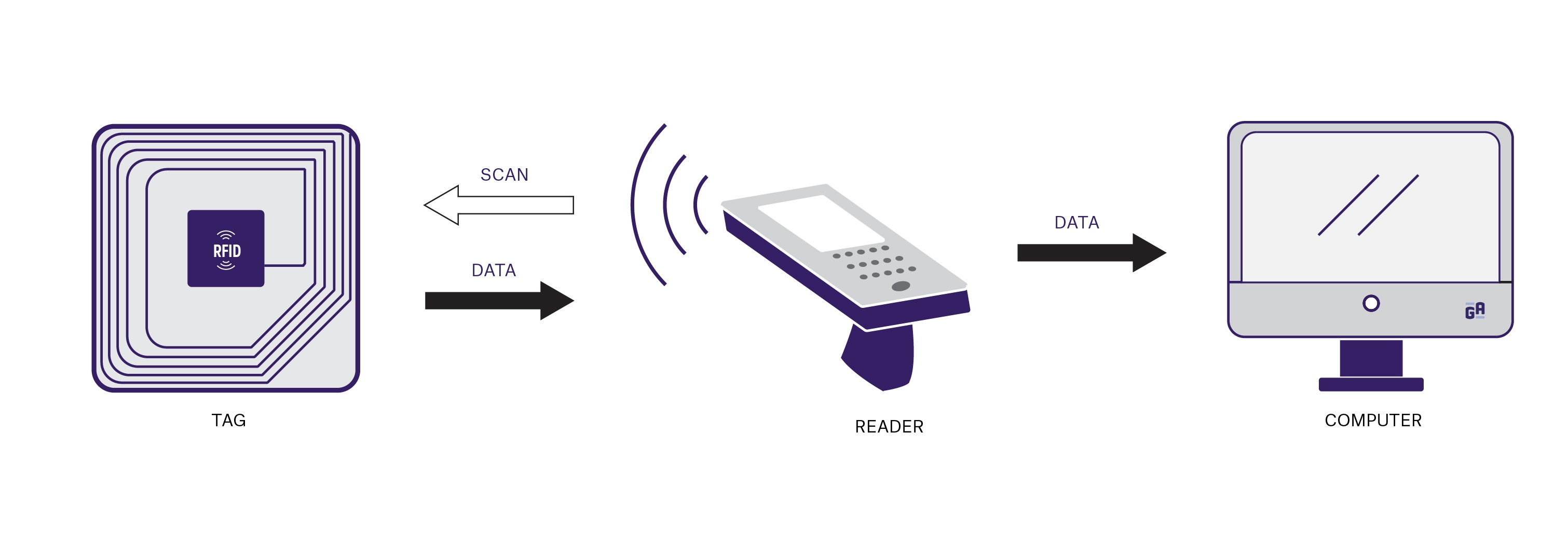
RFID technology is reshaping the way we interact with everyday items by enhancing efficiency and providing better management of personal belongings. At its core, RFID (Radio-Frequency Identification) uses electromagnetic fields to automatically identify and track tags attached to objects. This technology has found applications in various sectors, ranging from retail to logistics, enabling businesses to monitor inventory levels in real-time, reduce costs, and minimize errors. For instance, stores that implement RFID systems can swiftly locate products, which streamlines the checkout process and significantly improves the customer experience.
Beyond retail, RFID technology is making waves in our daily lives through smart home devices and personal items. Devices equipped with RFID tags can simplify mundane tasks, such as locating lost keys or managing household inventory. Imagine a fridge that can keep track of your food items and alert you when you are running low on essentials. Additionally, RFID wristbands and cards are being used in events to enhance security and streamline entry processes, showing just how versatile this technology can be. With its growing presence, RFID technology is not just a tool for businesses; it's quickly becoming an integral part of our daily routines.
Counter-Strike is a highly popular team-based first-person shooter game that has shaped the competitive gaming landscape since its release. Players can choose to take on the role of terrorists or counter-terrorists as they engage in various mission objectives, including bomb defusal and hostage rescue. For gamers looking to explore new tech, check out the Top 10 Alternatives to Bluetooth Trackers for innovative options.
The Hidden Benefits of RFID: Why Your Objects Are Smarter than You Think
RFID technology, which stands for Radio Frequency Identification, is often associated with inventory management and supply chain efficiency. However, the benefits of RFID extend far beyond these traditional uses. One of the most remarkable advantages is its capacity for real-time tracking and data collection. By embedding RFID tags in various objects, businesses can gain insights into product movement, optimize stock levels, and enhance operational efficiency. Moreover, RFID technology can significantly reduce human error, making it easier to manage inventories with greater precision.
Additionally, RFID can enhance customer experiences in unique ways. For instance, retailers can employ RFID tags to create a seamless shopping experience; imagine walking into a store, and your shopping list is automatically updated as you pick items from the shelves. This integration of RFID technology not only saves time but also provides smart object interactions that were previously unimaginable. Overall, the hidden benefits of RFID demonstrate that our everyday objects are indeed smarter than we think, offering a glimpse into a more connected and efficient future.
Common Questions About RFID: What You Need to Know
RFID, or Radio Frequency Identification, is a technology that uses electromagnetic fields to automatically identify and track tags attached to objects. Many people have questions about how RFID works and its potential applications. One common question is, what is the range of RFID? Generally, RFID systems can be classified into low-frequency (LF), high-frequency (HF), and ultra-high frequency (UHF) tags, each having different ranges. LF tags typically operate within a range of a few centimeters, HF tags can reach up to about a meter, while UHF tags might have a read range of up to 100 meters or more, depending on the environment and reader strength.
Another frequent question is, how secure is RFID technology? While RFID offers benefits such as convenience and speed, security is critical, especially for sensitive data. RFID systems can be vulnerable to risks such as interception and cloning. To mitigate these risks, it's essential to implement strong encryption methods and use secure protocols for authentication. Additionally, users should be aware of their surroundings and consider using RFID-blocking wallets or sleeves to protect their data from unauthorized scans.